Embark on a secure deployment journey with our blog—a deep dive into DevSecOps practices while deploying a Hotstar clone on AWS. 🚀
Uncover the intricacies of Docker, Jenkins, Java, SonarQube, AWS CLI, Kubectl, and Terraform as we automate, secure, and streamline the deployment pipeline. Learn the art of crafting an AWS EC2 instance, fine-tuned with Ubuntu and specific IAM roles. Discover the power of Jenkins jobs for Amazon EKS cluster creation, Hotstar clone deployment, and integrated security measures. 🔒
Explore the layers of security through SonarQube, OWASP, and Docker Scout, fortifying your application against vulnerabilities.🛠️🔐
Prerequisites:
AWS account setup
Basic knowledge of AWS services
Understanding of DevSecOps principles
Familiarity with Docker, Jenkins, Java, SonarQube, AWS CLI, Kubectl, Terraform, Docker Scout
Project Execution Steps:
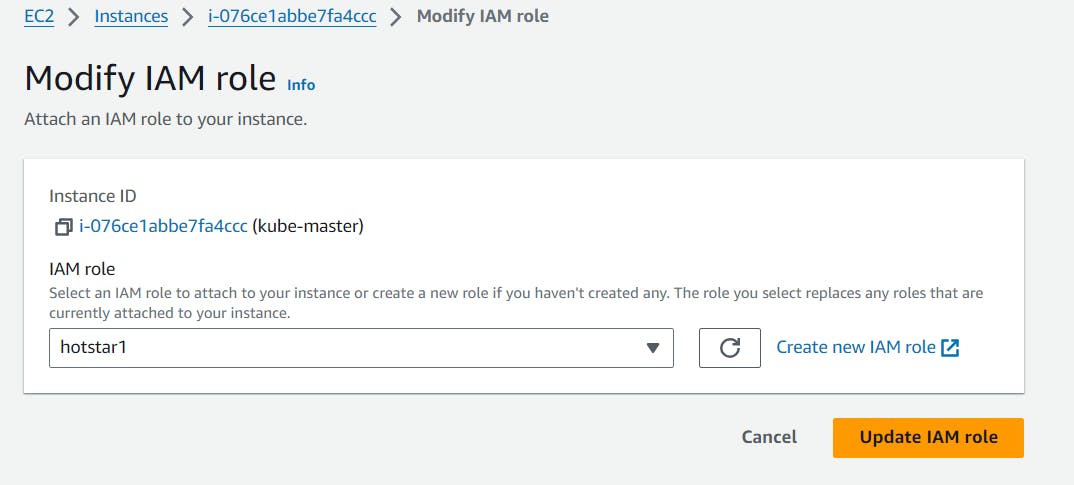
1. EC2 Instance Setup:
Setting the stage with an EC2 instance, we assigned it an IAM role, tailor-made for learning purposes.
2. Tool Installation:
Installed a toolkit comprising Docker, Jenkins, Java, SonarQube, AWS CLI, Kubectl, Terraform, and Docker Scout on the EC2 instance.
3. Jenkins Configuration:
The spotlight then shifted to Jenkins, where we meticulously configured plugins to seamlessly integrate with our toolkit.
4. Jenkins Job - Terraform EKS Cluster:
Introduced a parameterized Jenkins job, "terraform-eks," orchestrating the creation and destruction of the EKS cluster using Terraform.

5. Jenkins Job - Hotstar Clone:
Delving deeper into Jenkins, we fine-tuned plugins, set up a SonarQube token, and established a webhook for our Hotstar job.
6. Pipeline Configuration:
Outlined a streamlined pipeline within the Hotstar job, ensuring a cohesive orchestration of deployment, quality checks, and dependencies.
7. Docker Container Deployment:
The moment arrived to deploy our application within a Docker container, adhering to the defined pipeline.
8. Quality Checks:
With a critical eye, we reviewed the console output in Jenkins, validating the execution of all pipeline stages and confirming code quality and dependencies.

9. Accessing Hotstar Clone:
Celebrated our progress by accessing the Hotstar clone application, courtesy of the public IP of the Jenkins server.
10. Kubernetes Cluster Configuration:
Elevated our setup by updating the Kubernetes context with cluster name and region, ensuring a finely tuned deployment.
11. Jenkins Kubernetes Setup:
Enhanced Jenkins with Kubernetes plugins, enriching the orchestration capability. The Kubernetes configuration file became a discreet secret in Jenkins credentials.
12. Kubernetes Deployment:
Evolved our pipeline to seamlessly include a dedicated stage for deploying the app to the Kubernetes cluster.
stage('Deploy to kubernets'){
steps{
script{
dir('K8S') {
withKubeConfig(caCertificate: '', clusterName: '', contextName: '', credentialsId: 'k8s', namespace: '', restrictKubeConfigAccess: false, serverUrl: '') {
sh 'kubectl apply -f deployment.yml'
sh 'kubectl apply -f service.yml'
}
}
}
}
}
14. Upon completing the job and adding the dedicated Kubernetes stage to our pipeline, the final orchestration unveils a meticulously crafted pipeline as below:
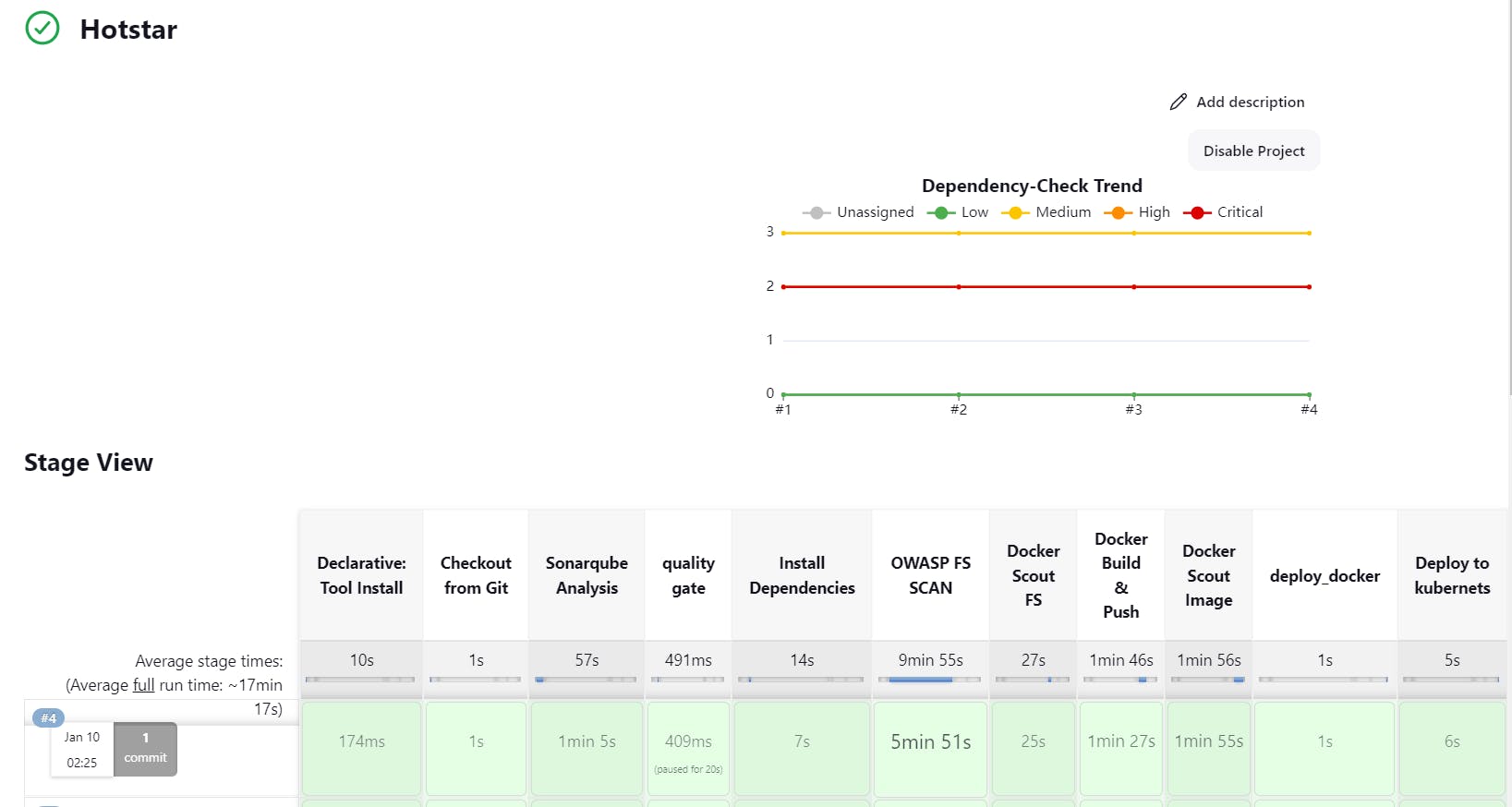
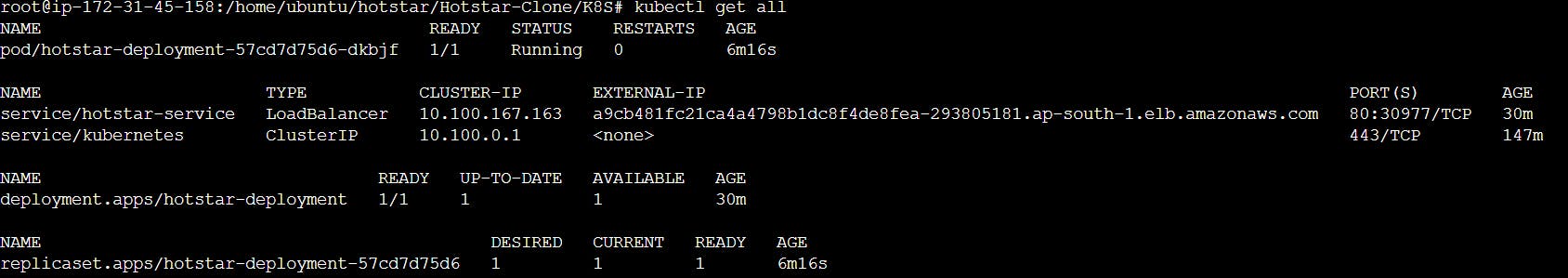
13. Verification:
Diligently verified the status of our deployed pods and services using the command "kubectl get all."
14. Accessing App on Load Balancer:
Culminated our journey by copying the load balancer DNS, witnessing the Hotstar clone app in all its glory.

15. Troubleshooting:
In the spirit of DevSecOps, we troubleshooted, ensuring our app opened seamlessly by checking and adjusting the load balancer port in the worker node security group.
Conclusion:
These steps encapsulate a hands-on exploration of deploying a secure Hotstar clone using DevSecOps principles. Each stage contributes to the robustness and security of our deployment process, setting the stage for future endeavors.
Closing Note: Unleash the Power of DevSecOps 🌟
Congratulations on completing this transformative journey into the realm of DevSecOps! We've navigated the intricate landscapes of AWS, Jenkins, Kubernetes, and more, sculpting a secure Hotstar clone. As you embark on your own projects, remember that DevSecOps is not just a methodology; it's a mindset—a commitment to excellence and security in every line of code.
If this blog sparked inspiration or proved valuable on your DevSecOps voyage, consider sharing it with your fellow enthusiasts. Together, let's empower the community to build secure, efficient, and innovative solutions. Your feedback and shared insights can be the catalyst for someone else's breakthrough.
Here's to continuous learning, evolving skillsets, and crafting a future where DevSecOps principles reign supreme. 🚀🔐
Ready to embark on your DevSecOps journey? 🚀